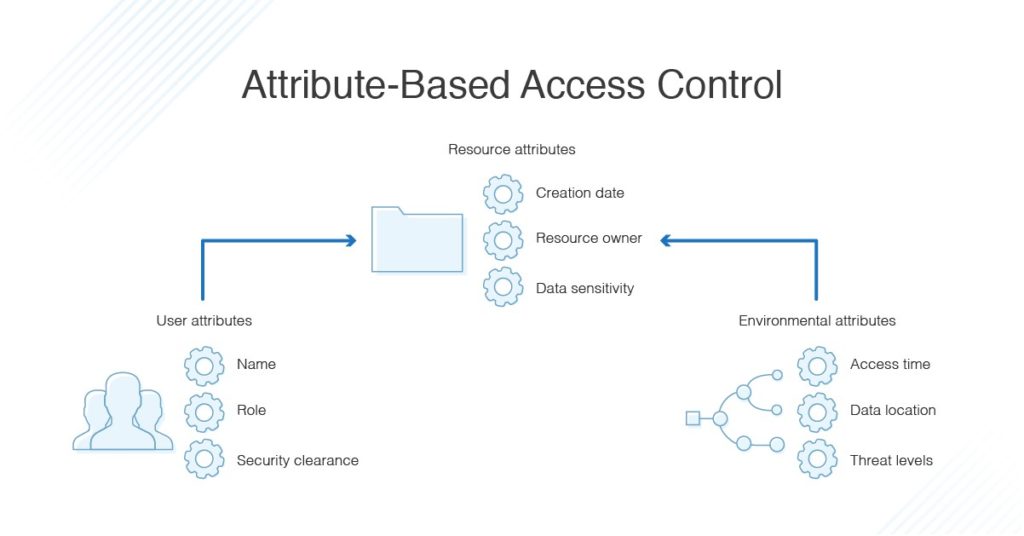
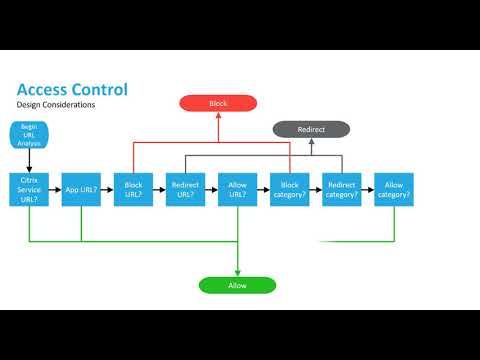
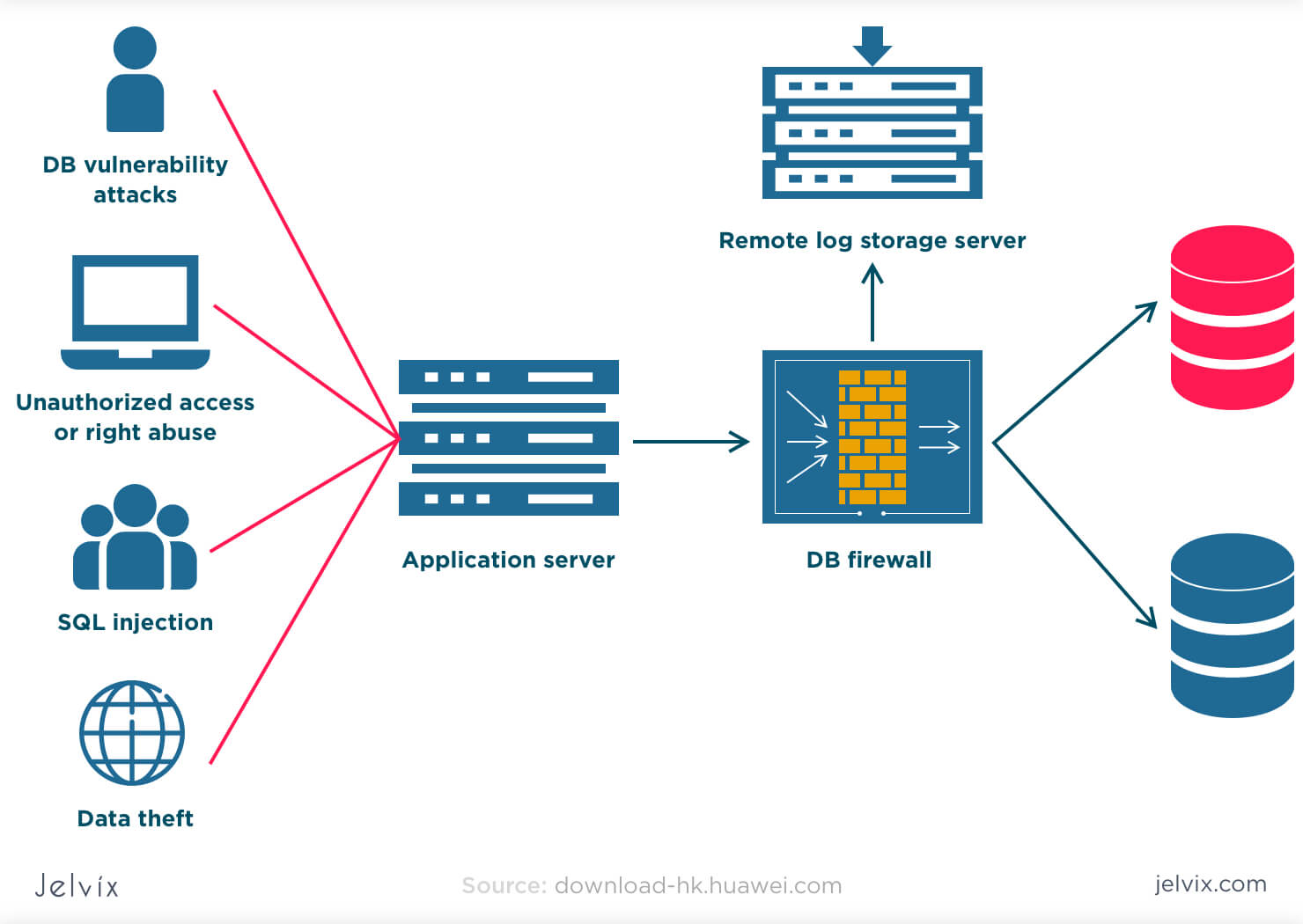
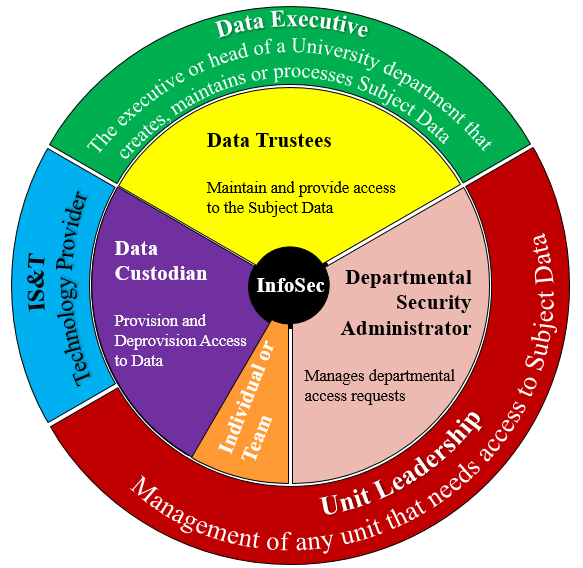
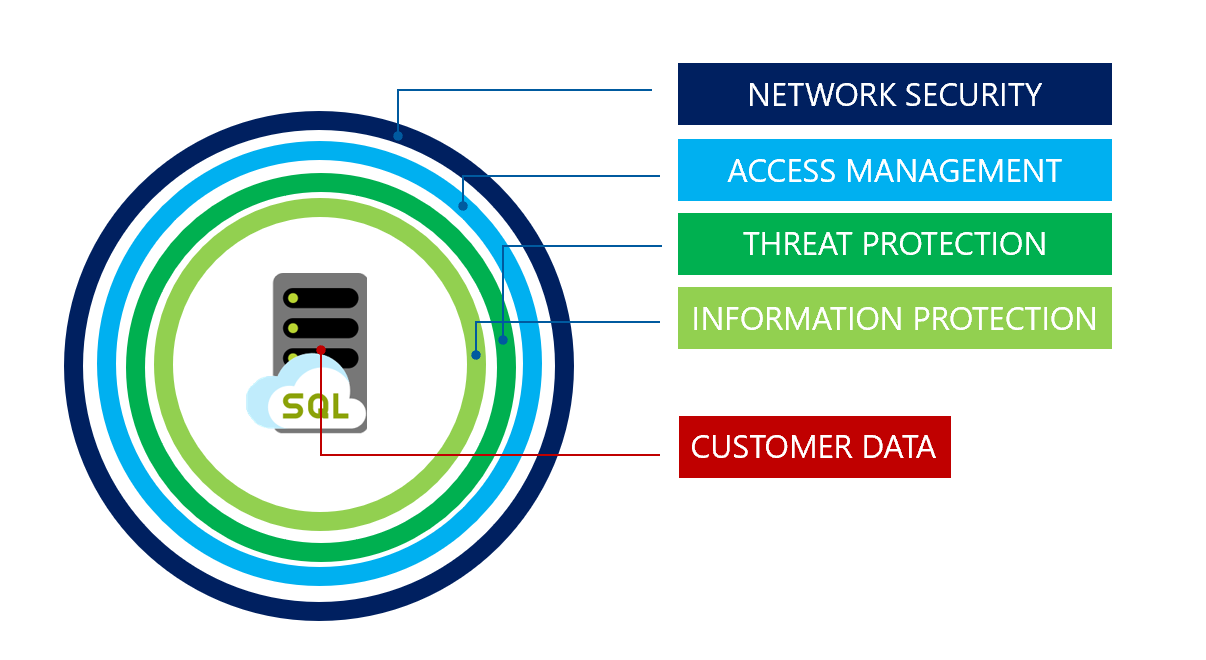
Multi-Authority Data Access Control For Cloud Storage System With Attribute-Based Encryption | Semantic Scholar
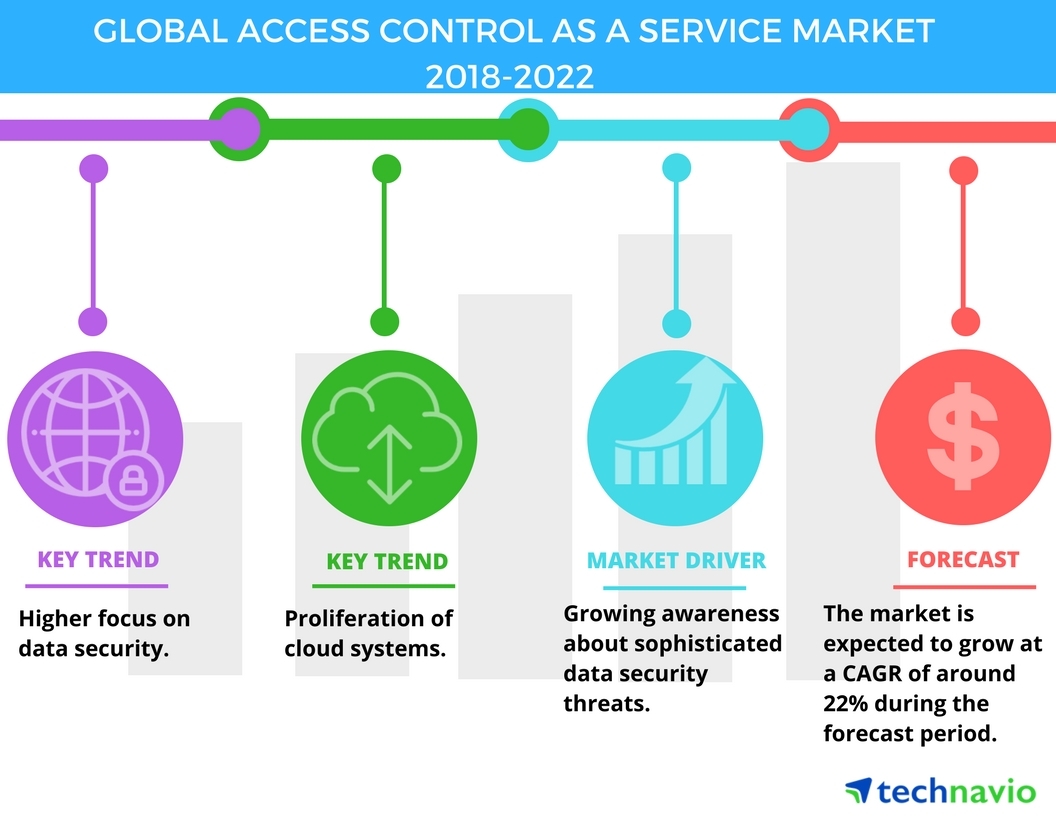
Global Access Control as a Service Market - Growing Awareness About Sophisticated Data Security Threats Drives Growth | Technavio | Business Wire